
The Final Document: More than a Report, an Action Plan
At the end of each penetration test, we summarize all our work in a complete and detailed document. The pentest report is the most important outcome of the process, as it not only identifies vulnerabilities, but also serves as a strategic guide to strengthen your security. In it, we highlight what your organization is already doing right, where it needs to improve, how the attacks were possible and - most importantly - how each vulnerability can be effectively remediated.
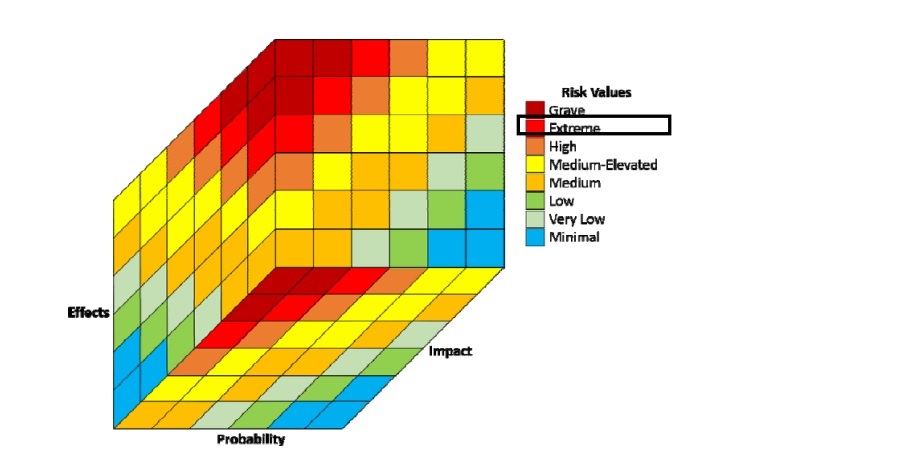
Our reports are based on a clear methodology, presenting the data in intuitive security diagrams and ensuring 99% accuracy of information. The structure is useful for both managers and technical teams:
Metodologia
Analysis Scope and Methodology
We start the report with a clear definition of the systems analyzed and their scope. We describe in detail the techniques and methods used, ensuring complete transparency about the work carried out.
Key Strengths
We believe that security also builds on what already works. Therefore, this section is dedicated to capturing and documenting the security controls and best practices that were identified and proven effective during testing.
Vulnerability Assessment Results
Here we present the full overview of the findings. We list and describe each vulnerability found during the analysis and sort them by criticality (critical, high, medium, low) so that the team can prioritize actions.
Detailed Evidence of Exploitation
For every reported vulnerability, we provide concrete evidence of its exploitation. This includes screenshots, code snippets and logs that unequivocally prove the steps taken to penetrate the system and the actual impact of the vulnerability.
Remediation Plan and Recommendations
This is the most strategic section of the report. For each vulnerability found, we provide detailed technical remediation guidance. Our recommendations range from configuration adjustments to suggested code changes so your team can act quickly and accurately to eliminate risk.
Process Summary
The document contains summaries for different audiences: an Executive Summary with an overview of the risks for the management, and a complete Technical Report that documents all phases and processes performed and serves as a detailed record of the entire pentest.